Author: Jochen Möller (Managing Director and CoFounder of EcholoN)
creation: 27.07.2023, last change: 19.02.2025
Table of contents
What are the benefits of a WebHook?
What is an HTTP request?
The advantages of WebHooks and their use cases
What is the risk of using webhooks?
How can you recognise the issue of data manipulation with webhooks?
Examples and use cases WebHook
How do I create a WebHook?
EcholoN CTI integration with a webhook
Webhooks are revolutionising the way we exchange data and information on the internet. But what is a webhook actually?
A webhook is a method of exchanging real-time information between applications. It involves sending a notification or signal from one application to another when an event or specific action takes place on the sending side. This means that the receiving application does not have to constantly make requests to the sending application to find out if there is new information.
The concept of a webhook is very simple: an application sends an HTTP request to a URL hosted by another application. The receiving application can process this request and perform appropriate actions.
Take, for example, a web shop that uses a payment gateway service. When a customer makes a purchase, the payment gateway sends a WebHook with the payment details to the specified endpoint in the shop application. The shop can then use this information to update the customer's order status or send notifications.
What are the benefits of a web hook?
The main benefit of web hooks is that they provide a faster and more efficient way of communicating between applications. Instead of constantly sending requests and waiting for a response, information is transmitted in real time. This saves time and resources and allows the application to react faster to changes.
What are the alternatives and what are the advantages and disadvantages?
Alternative methods to exchange data between applications are, for example, APIs or RSS feeds. The advantage of webhooks over these alternatives is that they provide a faster and more direct way of communication. APIs often require more complex implementation and continuous querying, while RSS feeds are not always reliable and often only support certain types of data.
What is the technology and structure of web hooks?
The technique and structure of web hooks are relatively simple. A sending application sends an HTTP request to a URL hosted by a receiving application. This request usually contains JSON data that contains specific information about the event or action that was triggered. The receiving application processes this information and performs appropriate actions.
What is an HTTP request?
An HTTP request, on the other hand, is a way for a client to request data from a server. The server responds to this request by forwarding the requested data to the client. The client in this case can be any device that has access to the Internet, such as a laptop, tablet or mobile phone that uses a web browser or third-party software programme.
For example, when you enter a website address into your browser, you send a GET HTTP request to the website server asking it to provide the content of the website. The server then sends a response with HTML, CSS and JavaScript code that your browser interprets and displays as a web page.
What are the differences?
Although both WebHooks and HTTP requests involve communication between two applications, they serve different purposes.
WebHooks are automated processes triggered by certain events in the application, while HTTP requests are initiated manually by a user, usually through a web browser.
WebHooks enable real-time communication between applications and can be used to automate tasks, while HTTP requests are better suited to situations where a user needs to access specific information from a server.
Understanding the differences between WebHooks and HTTP requests is essential for organisations that want to improve efficiency by streamlining communication between their systems.
The advantages of WebHooks and their use cases
WebHooks are becoming increasingly popular in software development for good reason. They enable real-time communication between applications and offer numerous advantages over alternative methods of data exchange.
The advantages of a WebHook
Real-time communication: WebHooks facilitate instant communication between applications. This means that applications can work together without delay, improving overall efficiency.
Less resource intensive: WebHooks consume fewer system resources than alternatives such as polling, which repeatedly requests information from the server even when no new data is available.
Automation: WebHooks allow businesses to automate processes by triggering an action when an event occurs in an application. For example, a shop can use WebHooks to automatically update its inventory when a new shipment arrives.
Alternatives to WebHooks
While WebHooks are useful, they are not suitable for every situation. In some cases, developers may consider other methods of data exchange such as polling or WebSocket.
Polling: Polling is a method of requesting data from a server at regular intervals. Polling is well suited for situations where real-time communication is not required, such as requesting stock quotes that are updated once a day. However, polling can be more resource intensive.
WebSocket: WebSockets enable real-time communication between server and client. They are well suited for applications that require bidirectional communication between client and server, such as chat applications.
Technology and structure of WebHooks
WebHooks use a simple structure to exchange data between two applications. When an event occurs in the source application, it sends a JSON payload to a specified URL endpoint in the target application. The payload contains information about the event, such as the type of event, the data associated with the event and any metadata.
What are the risks of using webhooks?
Using webhooks comes with some risks that should be considered during implementation and management. Here are some of the major risks associated with the use of webhooks:
Security risks:
- Data integrity: webhooks transmit data over HTTP, which can be vulnerable to tampering. It is important to ensure that the transmitted data is not altered in transit.
- Authentication and authorization: without proper security measures, unauthorized third parties could trigger webhooks or access sensitive information. Implementing authentication and authorization is critical to prevent unauthorized access.
- DoS attacks: If a webhook endpoint is not adequately secured, it could be vulnerable to denial-of-service (DoS) attacks, in which a large number of requests are sent to overload the service.
Data leaks:
- When sensitive data is transmitted in webhooks, there is a risk of data leaks, especially if the communication is not encrypted or if the data gets to the wrong recipient.
Misconfiguration:
- Errors in the configuration of webhooks can lead to unexpected behavior. For example, a misconfigured URL could cause webhooks to be sent to the wrong endpoint.
Unprocessed errors:
- If the receiving application or webhook endpoint does not properly respond to or handle errors, important notifications or data could be lost
Third-party dependencies:
- When you use webhooks to integrate with third-party services, you depend on the availability and reliability of those services. If the third-party service goes down or makes changes, it may affect your application.
- To minimize risks when using webhooks, best security practices should be implemented. These include, for example, using HTTPS and validating content via HMAC (HMAC - Wikipedia) to prevent tampering. The authentication and authorization of webhook requests, which can be implemented using HMAC in combination with a reverse proxy, for example. The logging of activities, which can be implemented, for example, by external security software such as a firewall or a reverse proxy, as well as the implementation of error handling mechanisms.
- In addition, webhook endpoints should be regularly checked for security vulnerabilities in order to identify and fix potential weaknesses.
How to detect the issue of data manipulation with webhooks?
Detecting data tampering with Webhooks requires careful monitoring and security measures. Here are some steps that can help you detect suspicious activity and data tampering related to webhooks:
Monitor traffic:
- Monitor inbound and outbound traffic at your webhook endpoint. Use logging and monitoring tools to log all webhook requests and responses. responses.
Validate data:
- Ensure that data received meets expected format and structure specifications. Illegal or unexpected data may indicate possible tampering.
Authentication and authorization:
- Use authentication and authorization to ensure that only authorized senders can trigger webhooks. This can be done using API keys, OAuth tokens, or other mechanisms.
Signature verification:
- Use digital signatures or HMAC (hash-based message authentication code) to verify the integrity of received data. If the signature is not valid, it could indicate data tampering.
IP whitelisting:
- Restrict access to your webhook endpoint to trusted IP addresses. This prevents access from unknown sources.
Rate limiting:
- Limit the frequency of webhook requests from individual senders to prevent DoS attacks or unwanted data overloads.
Monitor for unusual activity:
- Set up monitoring systems to detect unusual or suspicious activity. This includes unusual data patterns, an increased number of requests, or unexpected changes in webhook endpoint behavior.
Regular security checks:
- Perform regular security audits of your webhook endpoint to identify and address potential vulnerabilities and security holes.
Logging of error and warning messages:
- Implement a logging system that captures errors and alerts related to webhook activities. This enables you to respond quickly to suspicious activity.
Suspicious incident notifications:
- Configure notifications to be triggered when suspicious activity is detected. This enables you to respond quickly to potential data tampering.
Early detection of data tampering associated with webhooks is critical to protect the integrity of your data and application. The above measures help identify suspicious activity and respond to it appropriately to minimize potential damage.
Examples and use cases WebHook
There are many use cases for WebHooks. Some examples are:
- Notifications: An application can use webhooks to send notifications to other application when certain events take place. For example, an e-commerce website can use webhooks to notify another application when an order is placed.
- Automation: Webhooks can be used to enable automation by sharing information in real time between applications. For example, a marketing automation application can use webhooks to receive customer information from another application that stores CRM data.
- Data integration: Webhooks can also be used to integrate data between applications. For example, an analytics application can use webhooks to receive data from another application that stores usage data.
- Web development: Webhooks are also useful in web development for passing changes to a website or web service to other applications in real time. For example, this can be useful for updating content or processing form data.
Using webhooks enables seamless integration and data exchange between different applications and services, which can automate processes and improve efficiency. It is important to note that the implementation and configuration of webhooks depend on the specific application and usually require some technical expertise.
Examples of the use of WebHooks in different industries:
- E-commerce: a shop may use WebHooks to update inventory when new shipments arrive or to automatically notify customers when the status of their order changes.
- Healthcare: A medical device manufacturer can use WebHooks to monitor the performance of their devices in real time so they can quickly identify and fix problems.
- Financial services: Banks can use WebHooks to automate the process of notifying customers of unusual account activity.
- Social media: Social media platforms make extensive use of WebHooks to notify users of new news, posts and updates.
In summary, WebHooks are a valuable tool in software development, enabling real-time communication between applications and automating processes, thereby improving efficiency. Although not suitable for every situation, WebHooks offer numerous advantages over alternatives such as polling. When companies understand the structure and technology of WebHooks, they can use this useful tool to streamline their systems and increase productivity.
How do I create a WebHook?
Creating a webhook can vary depending on the application and programming language used. Here is a general guide to creating a webhook:
- Create a URL endpoint that will process the receiving data. You can create a custom URL endpoint on your own website or on a third-party service.
- Define the event that will trigger the webhook. In most cases, you can select or set the event in the application from which the webhook originates.
- Create the HTTP request that will be sent to the URL endpoint when the event is triggered. This request should contain the data you want to submit and be encoded in JSON format.
- Process the data in the URL endpoint once it has been received. In most cases, you will need to decode the data and process it in the application.
- Return an acknowledgement to the sending application to confirm that the data has been received and processed.
Examples of how to implement a WebHook
Example WebHook
POST request an yourapi.example.com/api/webhook
/8e266dd3689844e58d2aa16e38f618aafe25b1b4b8de4847b5ad9f76c5b44a2a
Webhook payload
{
"serialNumber": "PLE654-6964-10261",
"error": "212-16-17"
}
result
{
"reference": "CASE-000181"
}
Here are some examples of how to implement WebHooks in common programming languages:
Webhook in Node.js
const express = require('express')
const app = express()
const port = 3000
app.post('/webhook', (req, res) => {
console.log(req.body) // Webhook User data
res.status(200).send('Webhook received successfully.')
})
app.listen(port, () => {
console.log(`Beispiel-App lauscht auf )
})
Webhook in Python
Python provides the package "flask" to create a web application that can handle HTTP requests, including WebHooks. To implement a WebHook in Python, you can use the following code:
from flask import Flask, Anfrage
app = Flask(__name__)
@app.route('/webhook', methods=['POST'])
def webhook():
print(request.json) # Webhook User data
return 'Webhook received successfully.', 200
if __name__ == '__main__':
app.run(port=3000)
By following these steps and implementing WebHooks using the code examples above, you can automate your application's processes and improve communication between your applications.
It is also important to implement security measures for your webhook to prevent unauthorised access. For example, you can perform authentication to ensure that only authorised applications can access the webhook.
It may be helpful to consult the documentation of the application from which the webhook originates for specific instructions and implementation guidelines.
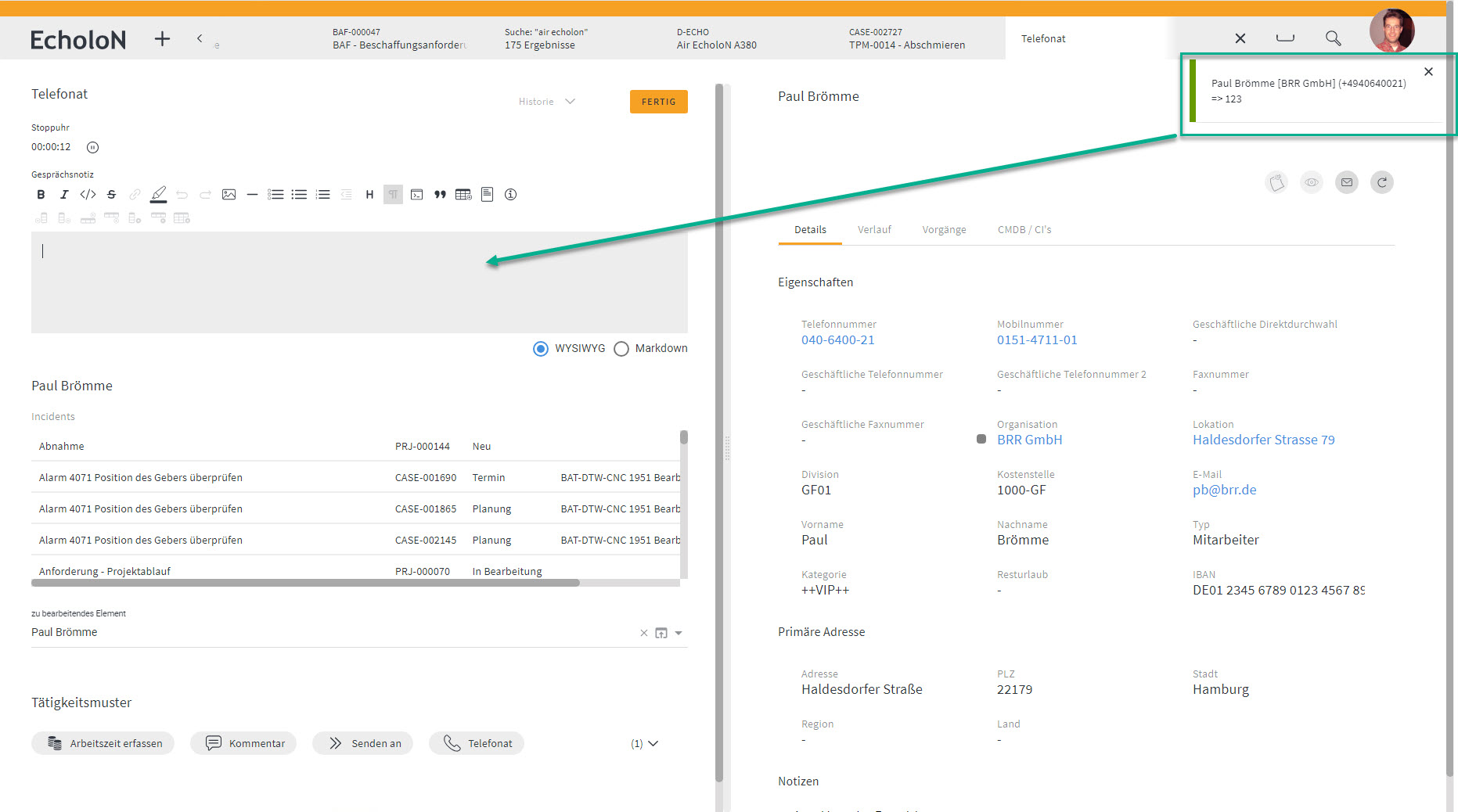
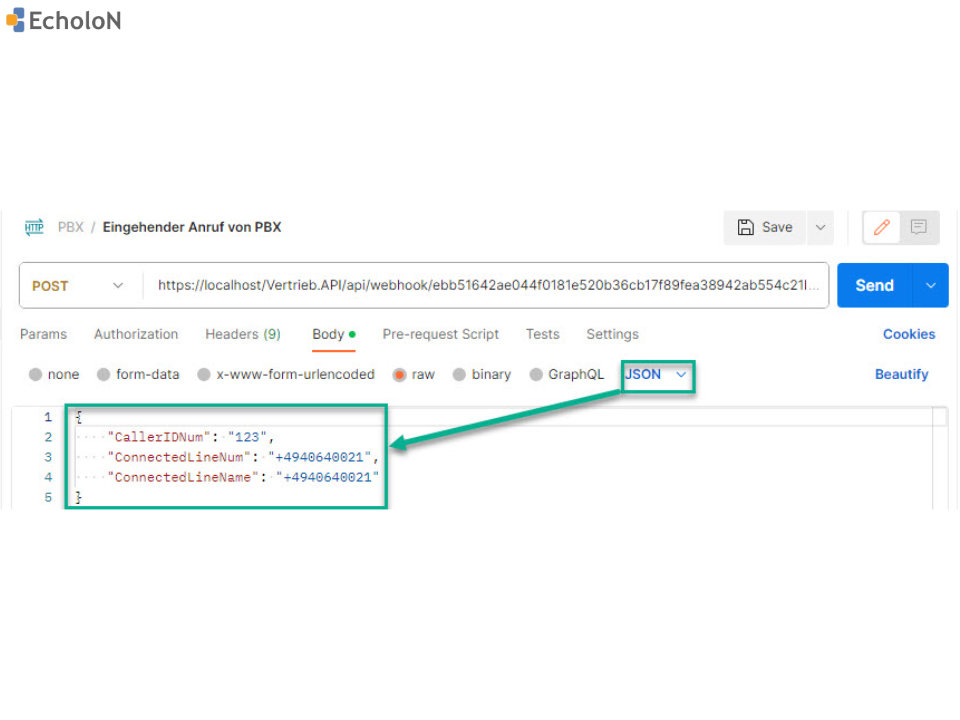
EcholoN CTI integration with a webhook
An EcholoN CTI integration with a webhook is set up as follows:
- Create a URL endpoint that processes the receiving data. This URL can be hosted on your own website or on a third party service.
- Define the event that will trigger the webhook. In this case, you can select the event that will be triggered when a call is received in the EcholoN CTI software.
- Create the HTTP request that will be sent to the URL endpoint when the event is triggered. This request should contain the data of the incoming call, such as call ID, caller number and called party number.
- Process the data in the URL endpoint as soon as it is received. In this example, you could store the received call data in a CRM system or send a notification to the appropriate staff member.
- Return a confirmation to the EcholoN CTI software to confirm that the data has been received and processed.
It is important to note that EcholoN provides an open CTI interface that facilitates the integration of third-party applications via webhooks. The EcholoN API documentation contains more information on how to integrate webhooks into the CTI integration.
Maybe also interesting:
- Blog article: What is GraphQL?
- Blog article: Microservices, micro-processes and API
- Blog article: Data Integration / DI / ETL
- Blog article: The MQTT protocol in the IoT - Message Queuing Telemetry Transport